Intel CET, security restarts from Tiger Lake
Intel Control-Flow Enforcement Technology Intel's commitment with CET is such that it can offer the devices that will integrate Tiger Lake a defense that at the software level would not be possible to implement: hence the desire to act at the hardware level, operating at a different level, with greater integration. But this is a long-range project, the foundations of which have been prepared since 2016 and following a close collaboration with Microsoft.
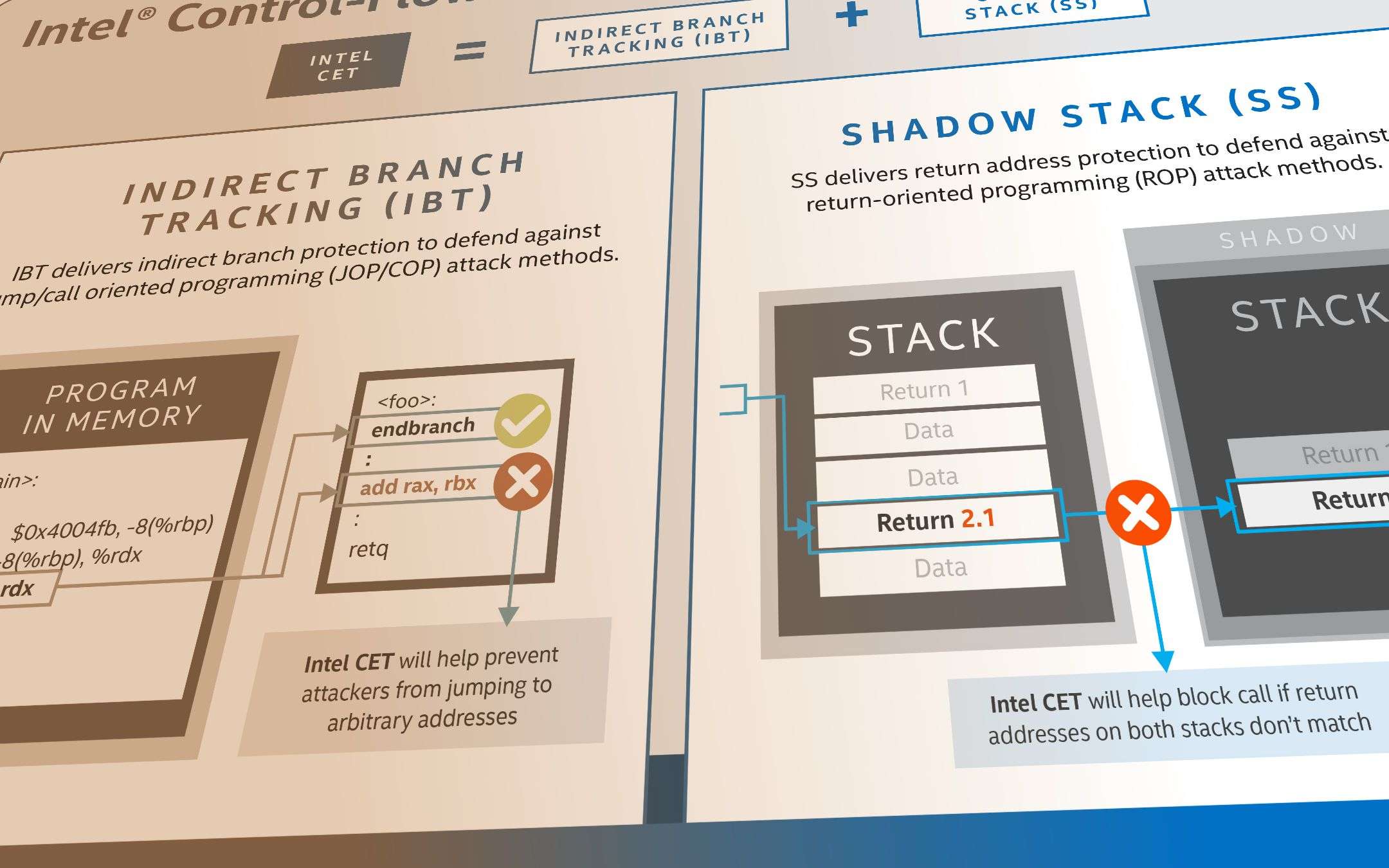
Intel CET is designed to protect systems from the incorrect use of legitimate code through control-flow hijacking attacks, commonly used by many types of malware. Intel CET offers software developers two features to defend against this type of attack: indirect branch tracking and shadow stack. Indirect branch tracking protects systems from attack methods based on jump / call-oriented programming (JOP / COP). Shadow stack protects return addresses from attack methods based on return-oriented programming (ROP). These attack methods are part of a malware class referred to as memory security issues, and include tactics such as stack buffer overflow corruption and use-after-free.
The importance of Intel CET lies in the fact that it is an integral part of the microarchitecture and is available on the whole family of products with that core. While Intel vPro with Intel Hardware Shield already meet and exceed the safety specifications for the PC Secured-core, Intel CET further extends the advanced functions of protection against computer threats. The availability of Intel CET is also planned for the future platforms, desktop and server.
Intel says it has carried out this challenge due to a growing number of threats that are putting at risk today's systems: it serves a greater hardware/software integration to be able to lock down the devices and the grip of Intel, CET, and Windows 10 is meant in the sense of a cooperative for this purpose.
With the “Control-Flow Enforcement”, in other words, Intel does not intend to only create a barrier to the malware, but the intention is to start a discourse of development which will further grow and deepen their capacity of defense: in dance there is only the safety of today, but also the strength of future mobile devices, whatever they may be, whatever may be their function (business or consumer), whatever the mode of use: “ Security solutions rooted at the hardware level, represent the best possibility of providing a guarantee of security against current and emerging threats. The hardware of Intel, and the additional guarantee of safety and innovation that brings with it, helps to strengthen the layers of the stack that rely on it “. A project for the long course, in short, that in Tiger Lake has a point of arrival, and the beginning of a new perspective.